“Enterprise Log Search and Archive” (AKA ELSA) is an open-source project started by an individual who needed the ability to not just collect logs from a bunch of devices but to also quickly search and parse them. And by a “bunch” I mean on the scale of millions and millions of logs. A lot of […]
Recently I had to produce some very high-level, general documentation for platform hardening. Boy, there isn’t much out there in terms of content when you start researching this topic out. Yes, there are lots of specific hardening docs for specific platforms but if you are like me and need to write generic “policies” or guidelines […]
Read about it more in detail here on Redhat’s site. This vulnerability affects all applications using certain versions of OpenSSL, so this is a cross-platform issue. This isn’t nearly as atrocious as Heartbleed was as there isn’t a chance of leaking your private keys. However, if you use Qualsys labs excellent SSL web scanner to […]
In a post Heartbleed world, implementation of SSL is being scrutinized like never before (at least in my short years of experience in information security). Even though Microsoft/IIS implementations were hardly, if at all, affected by Heartbleed, they do often suffer from other common SSL vulnerabilities. This is particularly true of Microsoft Server 2003 R2 […]
Currently I am looking into a couple of different cloud platforms for new infrastructure projects. Microsoft Azure is creeping up rather highly on the list. A few years ago the concepts of “security” and “cloud hosting” were diametrically opposed in many people’s minds. Security is an ironic field of IT in that technology, vulnerabilities and […]
Free penetration testing tools abound. Free, easy-to-use penetration testing tools… not as much. Free, easy-to-use, web-hosted penetration testing tools, rarer still. I came across an excellent, web-hosted NMAP port scanning tool and I wanted to make sure I linked it here in case I needed it again in the future. Without further ado… https://pentest-tools.com/discovery-probing/tcp-port-scanner-online-nmap I […]
I have already discussed Heartbleed in detail and have provided instructions on how to close the hole on affected server. Now that the hole is closed the final step is changing your server’s private key and “re-keying” your SSL certificates. Re-keying simply involves creating a new certificate signing request and sending it to your (most […]
Recently we had to wrestle with the Heartbleed bug. Heartbleed, was/is a major flaw in certain versions of OpenSSL, which is itself an “open source” project/application/codebase… This has had all of the armchair developers (myself included in that mix) either defending the concept of open-development or attacking it on grounds that it is less secure. […]
Heartbleed was a major vulnerability in the SSL protocol used by many many sites and services. Folks have been scrambling to patch it up quickly since it was announced a few days prior. If you are in the process of doing just that for yourself or your organization, you might be so busy fixing websites […]
The Heartbleed bug is what I would professionally classify as seriously scary stuff. Basically there is some kind of heartbeat functionality built into OpenSSL. Often, in tech talk, this kind of thing is used for remote service monitoring (i.e. if I have a pulse my service is at least up). In this case, I am […]
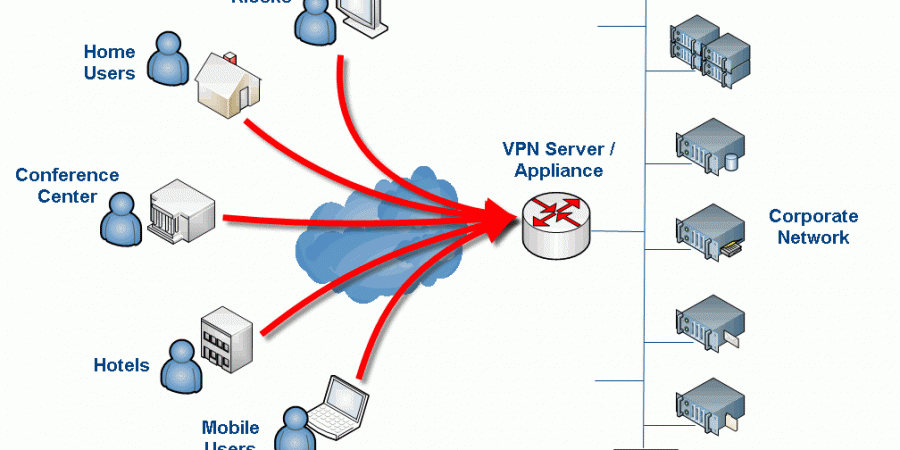
Thought I would post this one quickly… Having trouble getting OpenVPN to start/work for you and you are seeing this error in your logs? “TCP/UDP: Socket bind failed on local address” The resolution is pretty simple. Try changing the port you have assigned to openVPN in your config file and restarting the service. Most likely […]
I am not sure when OpenVPN added multi-factor support to their Access Server but I am thrilled that they did. It must have been recently (within the last few weeks or months) as I was using OpenVPN Access Server about 4 months ago as a temporary solution while my main solution was down and it […]
After having already gotten a full page into writing a walkthrough (not to mention hours already spent with Authy) I found out that Authy will NOT WORK with OpenVPN and LDAP authentication unless the folks at Authy customize the ldap module for you. Which requires enterprise support, at a retail price of $500/month! Which was […]
INTRODUCTION I wrestled with getting OpenVPN to work with Microsoft Active Directory authentication better part of 2 days. I was surprised that it was so hard to find a straightfoward tutorial on the topic that actually worked! I had to do a lot of Google-Fu and look at many different pages to put together what […]
- « Previous
- 1
- 2
- 3