Client Configuration and Installation
So at this point you should have your firewalls all opened up, and your server configured with the correct IP address and Port number and ready to accept clients using key authentication. If you think this is getting to be a long tutorial, it is. I know because I am the one typing it out :). However the length is partly necessary as I wanted to put something together that included all the code one would need to get this done. Let’s keep moving.
The next step is to get your client machine properly configured to make a connection. That means you need to get the open-source free version of OpenVPN for Windows (I am assuming Windows clients as the goal here is to use AD authentication). I found this confusing at first as there isn’t a clear explanation anywhere that the OpenVPN “SERVER” software for windows is also the client software. At least on the community edition (free) side. To further confuse things, the paid “Access Server” version has its own client that, as far as I can tell, doesn’t work with the community edition of the server. But that is exactly the case. So, hop on over to this page and download the latest “windows installer” package (get the correct 32-bit or 64-bit version) to your client computer: http://openvpn.net/index.php/open-source/downloads.html
Run the installer. Leave the default components selected for install. When you get to the destination folder screen, I recommend moving the destination to a new folder on the root of the C:\ drive. Otherwise your users are going to have to run the OpenVPN client with elevated permissions in order for some things to work correctly.
Once it is finished installing, use windows explorer to navigate to the directory where you installed it. In my case I put it in c:\OpenVPN\.
Go into the config folder. You will note it is currently empty. That is because the client must have a unique config file for each server it is going to access and certain settings must match those of the server. Furthermore, inside of this folder you are going to have to have a few different key files that need to be copied from the OpenVPN server.
They recommend a secure method of copying the keys. MY PREFERRED METHOD is to “cat” the key files (cat command basically just displays the contents of a file in linux directly in the shell) in a putty SSH session, highlight the text and copy it into a new text file on my windows machine and save the file / change the file extension to match. If you are doing this, I recommend you tell windows to not hide file extensions (start menu –> in the search bar type “show exten” and wait –> select “Show or hide file extensions” –> opens up folder options –> untick “hide extensions for known file types”). I also recommend you download and install “notepad++” for handling these files as, unlike notepad, it will not add undesirable things to files (like empty lines and characters).
Okay, so here we go…
On the client machine, create a new text document in the OpenVPN\config folder. Right-click it and say you want to edit with notepad++ (or notepad will usually work).
From your SSH shell session into the OpenVPN server, type the following:
And out will print something like this (do not copy this, each ca.crt is unique, this is fake, just an example)
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
ChMKQnJpZGdldHJlZTETMBEGA1UECxMKYnJpZGdldHJlZTEWMBQGA1UEAxMNQnJp
MjJJouCnHI8wQyrxOW4rWIX5iF7uWdFXaAibC12cG4xLDAqBgkqhkiG9w0pY2VzQ
MIIFCTCCA/GgAwISIb3DQEBBQUAMIGzMQswCQYDbC12cG4xLDAqBgkqhkiG9w0pY
VQQGEwJETMBE65zfsEa29sLXZwbjDbC12cG4xLDAqBgkqhkiG9w0pY2VzQGJyaWR
-----END CERTIFICATE-----
You need to copy that whole block (including BEGIN CERTIFICATE and END CERTIFICATE lines) into your blank text document on your client machine. If you are using Putty and an SSH shell, you just highlight it to copy it. Then paste it on your client machine’s empty text file. Save the text file on the windows machine, close it, and rename it to “ca.crt” (dropping the txt extension).
You can also copy these files over any other way you can think of (USB key, email, etc.) but you are on your own as far as how to do so. This is my method and I think it is secure as I am copying over an SSH session.
Rather than go through the rest of the files like I did with this one, I will just list the “cat” commands to display them and you can create a new text document on your client machine for each and then rename it to match the file on the OpenVPN server.
cat /etc/openvpn/easy-rsa/keys/client1.key
cat /etc/openvpn/ta.key
Okay, once you are done with that, make one more NEW text document inside of the openvpn config folder on your client machine and copy and paste the following verbatim into it.
port XXXX #CHANGE THIS
proto udp
client
float
dev tun
ca ca.crt
tls-auth ta.key 1
cipher AES-128-CBC
comp-lzo
ping 10
persist-tun
persist-key
verb 4
#CHOOSE AUTHENTICATION TYPE
#AD/PASSWORD AUTHENTICATION
#auth-user-pass
#auth-nocache
#KEY AUTHENTICATION
cert client1.crt
key client1.key
There are two lines marked “change this” for the IP address and Port number of your OpenVPN server. You need to know the public IP address of your OpenVPN server (or url if you are using DNS) if you are making a VPN connection over the internet (i.e. not across a local network). Explaining this further gets outside of the scope of this article. Suffice to say, your openVPN server needs to probably have NAT’ing to a public IP address from your one network that you are trying to access and that public IP address must be accessible from the client machine. Specify the port as well that you set your OpenVPN server to respond on. Save the file.
Rename the file in windows to “openVPNclient.ovpn” (once again dropping the .txt extension).
Once all of the above is said and done you should have the following on your Windows client computer:
- C:\openVPN\config\ca.crt
- C:\openVPN\config\client1.crt
- C:\openVPN\config\client1.key
- C:\openVPN\config\ta.key
- C:\openVPN\config\openVPNclient.ovpn
And you are now all setup to attempt a connection using key authentication. If this works, you can move on to setting up Active Directory Authentication!
To try your connection, on your client machine, open up the “OpenVPN Gui” application. It must be right-clicked and “run as administrator”. You should get a new icon in your taskbar that looks like two computer monitors with red screens. Right-click on that and hit “connect”.
Subsequent runs of OpenVPN GUI will also require the “run as administrator” option. This can be gotten around though and will deal with this in another article. For enterprise applications, often users only have user level access.
Your windows firewall may pop up and give you a warning. Hit allow access. After a few moments you should get a notice from your taskbar that looks something like this:
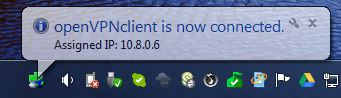
If so, you are doing great! Key authentication is working and we can move on to setting up active directory authentication!

Just an FYI, one of the commands after the second to last reboot prevents any connection to the Linux server
That’s interesting, do you know which command or configuration item is killing the connection? I am wondering if I fat-fingered something somewhere in the write-up. It has been a while since I worked on this. I know when I was testing that VPN connectivity still worked and that the final result was “no split-tunneling” i.e. proxy client machines had all traffic forced through the VPN tunnel. What I am not sure is if I somehow broke SSH connectivity but didn’t realize it because I was working on the machine directly (i.e. not remotely via SSH).
If you can shed some light on this so I can fix the write-up that would be awesome. Hate to have anyone breaking things on there end 🙂
Thanks for the heads up!
Yeah so basically for some reason, doesn’t make sense to me, adding that entry into the iptables and setting the file to load upon restart locks out any connection in, the system i implemented this in is in azure so remote access is the only option, it’s most probably a requirement to add an accept for SSH?
adding the entry without setting the file to load upon restart doesn’t cause any issues (as far as i can tell haven’t checked thoroughly enough)
great post, really love it!
greets, Wilfried
I did it but start openvpn is failed .
openvpn-auth-ldap plugin is 2.03 and download using “yum instal openvpn_auth-ldap.x86_84” on Centos 6
Thanks for this guide. I suggest copy and past attributes from AD directly into “/etc/openvpn/auth/auth-ldap.conf” . This was my issue. Good luck
This saved me a ton of time. Thanks for taking the time to post it.
Just wonder is there a way to secure client certificate from being compromised and used from another PC ?
cp server.crt server.key ca.crt dh1024.pem ta.key /etc/openvpn/
here should dh1024 should be changed to dh2048 i believe
Great article! Helped me a lot! Little supplement: Add the following to your server.config:
push “dhcp-option DOMAIN fqdn.yourADDomain.com”
Otherwise a had to use the fullname e.g. servername.fqdn.mydomain.ch to contact my internal infrastructur.
Thanks! Appreciate the tip as well 🙂 – Sure it will help others. OpenVPN Community Edition is honestly a bit of a bear. I finally gave up and just moved to the paid version (which is relatively cheap vs. other similar solutions) which is like a completely different product from an administrative perspective. The thing I really needed was two-factor authentication and the community edition (at the time) was very hard to get setup with this.